Overview Before you can defend a system, you need to understand what makes it weak. This lesson defines the term “vulnerability” in cybersecurity, clarifies how it differs from threats and exploits, and introduces the foundational concept of the CIA triad—Confidentiality, Integrity, and Availability.
Definition of a Vulnerability A vulnerability is any flaw, misconfiguration, or weakness in software, hardware, or processes that can be exploited to compromise:
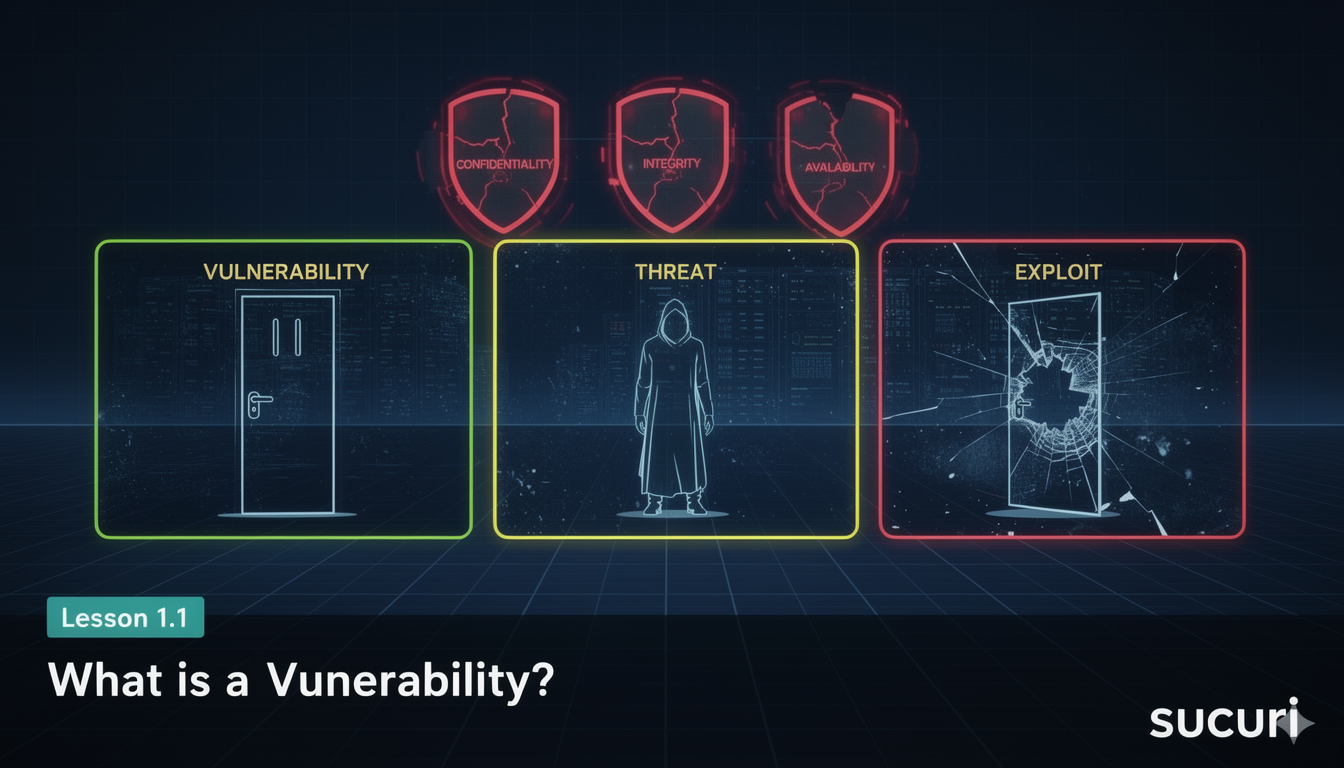
- Confidentiality – Unauthorized access to sensitive data
- Integrity – Unauthorized modification or corruption of data
- Availability – Disruption or denial of access to systems or services
If a weakness can be used to break any of these three pillars, it qualifies as a vulnerability.
Vulnerability vs Threat vs Exploit Let’s break down the relationship:
|
Term |
Definition |
|
Vulnerability |
A weakness in a system |
|
Threat |
A potential actor or event that could exploit a vulnerability |
|
Exploit |
The actual method or code used to take advantage of a vulnerability |
Analogy: A vulnerability is an unlocked door. A threat is a burglar who might walk through it. An exploit is the act of breaking in.
Examples of Vulnerabilities
- Software bugs: Coding errors that allow unintended behavior
- Unpatched systems: Outdated plugins, themes, or OS components
- Misconfigurations: Weak passwords, exposed databases, permissive file permissions
- Human error: Mistakes in setup, maintenance, or access control
Why Definitions Matter Not every risk is a vulnerability. For example:
- A server being “old” is not inherently a vulnerability.
- But if that server runs unpatched software with known CVEs, it becomes one.
This distinction helps prioritize remediation. Security teams focus on weaknesses that are exploitable—not just theoretical risks.
Industry Standards
- CVE (Common Vulnerabilities and Exposures): A standardized identifier for known vulnerabilities.
- CVSS (Common Vulnerability Scoring System): Rates severity from 0.0 (none) to 10.0 (critical).
- OWASP Top 10: A widely accepted list of the most critical web application vulnerabilities.
Key Takeaways
- A vulnerability is a weakness that can be exploited to impact confidentiality, integrity, or availability
- It’s distinct from threats (potential danger) and exploits (actual attack methods)
- Understanding this definition is foundational to patching, auditing, and securing systems
- Industry frameworks like CVE and OWASP help classify and prioritize vulnerabilities
